Devices connected via IoT technology are spreading across multiple industries at unprecedented rates. But the benefits of enhanced connectivity are accompanied by increased security risks.
IoT technology is used in everything from healthcare devices, to transportation infrastructure, to industrial control systems supporting operationally critical processes.
According to Forbes, some 80 billion devices will be connected to the internet by the year 2025. In terms of customer convenience and effective performance, this trend could be game-changing for people who rely on technology to explore, work, and live.
But at the same time, the same connectivity and analytics processes that create that convenience can also open devices up to potential attack and exploitation of security vulnerabilities.
And the volume of IoT attacks capturing the headlines make it clear that the risk is very real and very concerning. This means that you have to be especially vigilant in your own development process and throughout your product’s lifecycle to make sure your devices have the proper security posture to keep your end-users’ intellectual property, sensitive user data, and other information protected.
Below are some important considerations to keep in mind when designing security into your embedded IoT system.
Internet of Things Device Security
Verifying Authenticity from Bootloader to User Applications
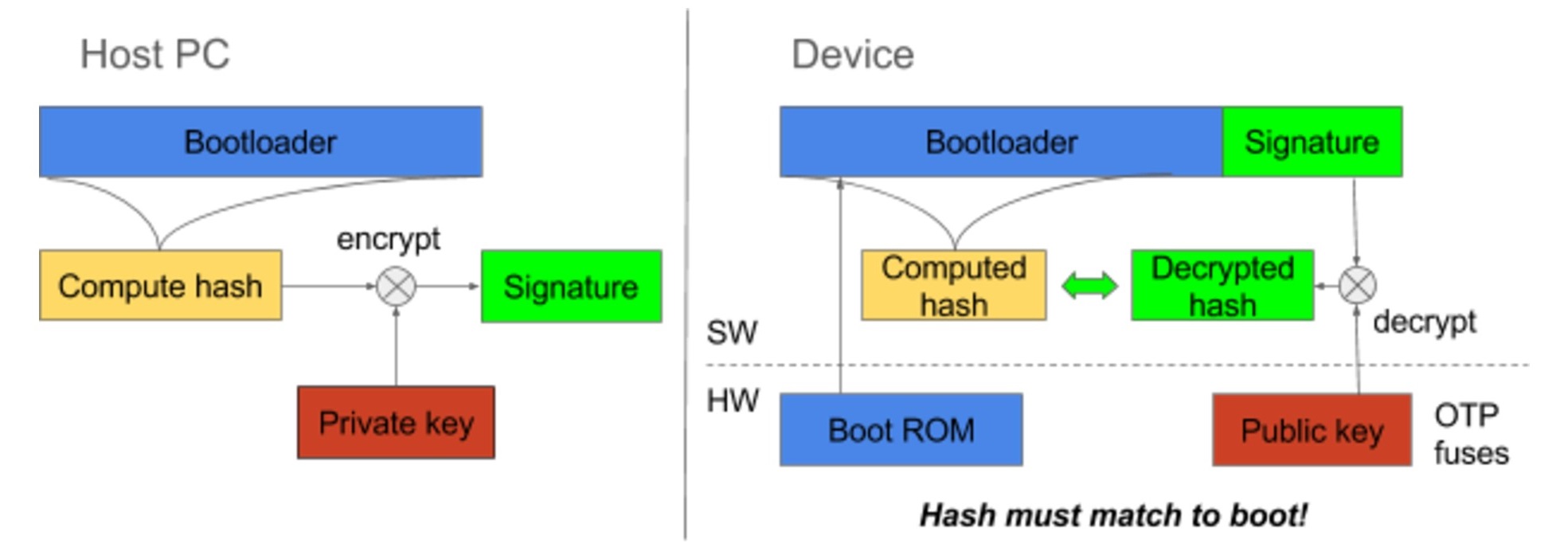
The security of your device can be threatened even in the moments it’s starting up — bootloaders have full control over your system, but are typically kept on unprotected storage, which could introduce exploit opportunities if it is not properly secured or validated.
To boot securely, your system should not allow unauthorized images to run, and must protect authorized images from being tampered with somewhere down the line. You then have to extend the chain of trust to span the entire system — the Linux kernel, root filesystems, and applications — to make sure there are no unprotected areas that are exposed to potential attack. Image authenticity can be verified using digital signatures as shown in the figure below.
Protecting IP and Data through Key Management and Encryption
Unfortunately, once your device is booted, all it takes is a cloned device for a hacker to launch a man-in-the-middle attack and intercept sensitive user data. In order to protect your device from being knocked off, reverse engineered, or counterfeited, you need to encrypt the data or software.
Of course, you also have to protect the key you use for encryption with a secure storage mechanism. And in general, software that handles confidential data should run from a Trusted Execution Environment (TEE) that has been configured to keep it secure.
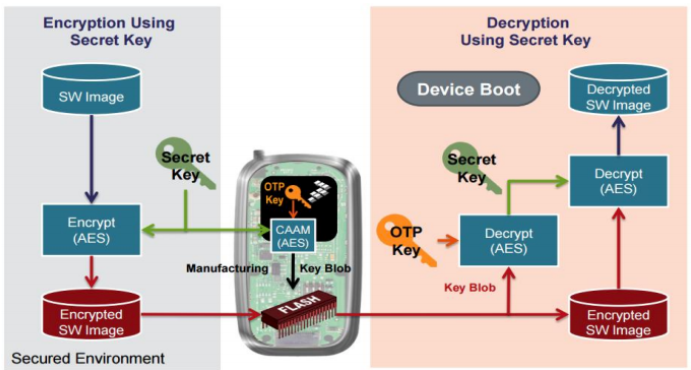
Image credit: NXP Semiconductors
The above figure illustrates how processor hardware capabilities can be leveraged to encrypt software and protect keys.
Auditing and Hardening
Unfortunately, no system is configured to truly defend against attacks by default. In conducting your device security risk assessment, you have to evaluate the security posture in relation to misconfigurations, deployment and user errors, and other unintended exposures and security gaps.
There are a wide variety of areas you’ll need to cover if you want to fully assess the security of your device. For example, is the boot process secure? Is access to storage protected?
Additional considerations are access control and enforcement, connectivity control, network security, and encryption key management.
Given the ubiquitous nature of open source components in devices, steps such as constructing an open source Bill of Materials inventory and conducting embedded Linux hardening have become increasingly critical.
Stay Secure: Vulnerability Management
In addition to misconfigurations, you’ll also have to be aware of the Common Vulnerabilities and Exposures (CVEs) that put your product at risk. In 2017 more than 14,000 CVEs were discovered, and the CVE list this year surpassed 100,000 back in April. As such, CVEs are a critical source of intelligence about potential weaknesses in your product, and need to be constantly monitored for, assessed, and patched.
Patch management is already a critical task. With CVE monitoring and vulnerability management in the mix, it can become even more challenging. And given the mission-critical nature of IoT, rapidly detecting and mitigating IoT device vulnerabilities is essential.
For an in-depth look at how to thoroughly monitor for and fix CVEs that apply to your specific device, check out our previous blog post.
Updating and Deploying Software OTA in Response to Vulnerability Reports
If your product is already in the field when you become aware of CVEs that put it at risk, you might have to develop a specialized, creative way to deploy updates to the product. Such update strategies must be equipped to deal with unreliable power sources and connectivity over the course of a long product lifespan (anywhere from 5-20 years depending on the type of device), and must in many cases be done remotely.
Over-the-Air (OTA) updates do have their challenges and it essential that you make it easy for your device end-users to perform updates and patching. For example, IoT devices are often deployed in a very large scale, often exceeding 50,000 devices in production. So the OTA update and patching processes need to accommodate this scale and the fact that some devices may be remote with limited connectivity.
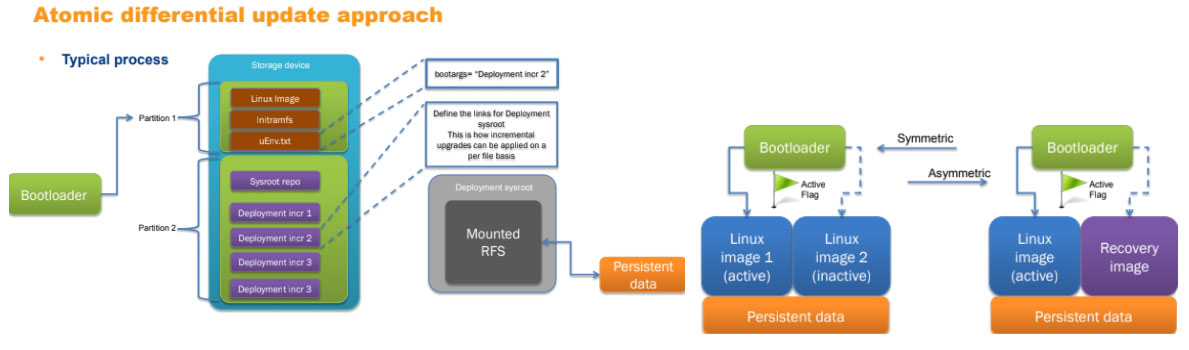
As shown above, IoT device constraints such as storage space, device up-time can dictate the design choice for underlying update mechanism such as differential updates or full image updates.
TRST Timesys to Look to the Future
Embedded system IoT device deployments are growing faster than traditional security practices can keep up. IoT introduces scale, distributed computing and devices with larger attack footprints than traditional IT.
Luckily, Timesys is already responding to these trends, and we’re making available the industry’s best practices for embedded system security when you are deploying open source components in your IoT devices.
“Reduce the Risk with RISC: Designing and Maintaining Secure Embedded Linux Devices with Advantech RISC Platforms,” our most recent webinar series, explains each of the topics discussed in this blog post in-depth to help engineers feel confident in their ability to secure their embedded systems. You can request the link to any of the recorded sessions here, and follow along with our experienced engineers as they share tips and industry best practices for designing and maintaining embedded IoT cybersecurity.
We’ve also unveiled our Threat Resistance Security Technology (TRST) Product Protection Solutions, designed to help you make sure your embedded products are secure by design, and stay secure throughout their lifecycle. No matter what stage of development you’re in, we have solutions tailored to your needs. Contact us to find out how to leverage our TRST service to keep your products safe.
About Timesys
Timesys has extensive experience with embedded system development and lifecycle management. Timesys has been instrumental in working with global leader semiconductor manufacturers with smart, quick and quality solutions for highly complex systems with accelerated product innovation and multiple product variants.