Responding to Recent Attacks with Vigishield In light of recent attacks on the open source community, we've been asked if or how our tools (specifically, Vigishield) could have helped prevent them from being successful. The two most recent attacks of interest were:...
Open Source Embedded Software Development and Security Blog
Securing Your Software: A Guide to SBOM Generation without Sources and CVE Scanning
Why Scanning for CVEs is Essential in Open Source Software Maintenance Scanning your open source software for CVEs (Common Vulnerabilities and Exposures) is a very important maintenance step for any software project. Generally, these CVEs are stored in publicly...
Everything You Should Know About Known Exploited Vulnerabilities (KEVs) and How They Differ From CVEs
What are Known Exploited Vulnerabilities (KEVs), and why should you care? As embedded Linux developers, we navigate a world of code, configurations, and complex systems daily. It's a universe where every line of code is a potential gateway for malicious actors seeking...
Elevating Your SCA Management with the Power of Vigiles-CLI
In the realm of Software Composition Analysis (SCA), the significance of robust tools cannot be overstated. To further elevate your experience with Vigiles, our comprehensive SCA tool, we're thrilled to introduce the Vigiles Command-Line Interface (CLI) - a...
What SBOM Generation Tool is Best for Your Python Application?
When creating a Software Bill of Materials (SBOM) for your Python application, one of the best tools to use is Syft. Recommended Tool: Syft Syft is a CLI tool and Go library for generating Software Bill of Materials (SBOM) from container images and filesystems....
Choosing the Right SBOM Tool: A Comparison of Top SBOM Generation Tools
Choosing the right SBOM generation tool for your needs can be a daunting and challenging task, given the wide array of options available and ecosystems to work within. A well-formed SBOM should: contain all the elements required for you to meet the NTIA “minimum...
Choosing the Right SBOM Generation Tool: Key Criteria for Evaluating SBOM Generation Tools
As you know, choosing the right SBOM generation tool plays a pivotal role in open source security, compliance, and project efficiency. The consequences of using an unsuitable tool can be severe, from incomplete or inaccurate information to missed security updates and...
Choosing the Right SBOM Generation Tool: Why is it a Critical Step in Open Source Security?
In today’s constantly evolving world of software development where the use of open source components has become the norm and vulnerability risks are a weekly hurdle, ensuring the security and compliance of your projects may seem like an impossible feat – but it is...
Securing Your AWS IoT Connection: A Guide to Using PKCS#11 on i.MX93 EVK
Following up on the blog PKCS#11 with OP-TEE, this blog dives deeper with a hands-on example of using PKCS#11 on an NXP i.MX93 EVK running Yocto based Linux to securely connect/provision the device on the AWS IoT platform. While...
Linux Kernel Security: dm-crypt with “trusted keys” using TEE backend
Background DM-Crypt is a disk encryption subsystem in the Linux kernel and can be used to protect sensitive data / intellectual property stored (IP) on external storage. For example, if an attacker copies the contents of the external storage media offline, they would...
Designing Yocto platforms for scalability and maintainability across product lines
Scaling software development is a perennial problem. As product lines grow, maintenance costs for device manufacturers can increase dramatically when software is ported and reused from one product to the next. This can balloon into major issues like security...
How to Actually Understand and Use the 6 Different Types of CISA SBOMs
What is an SBOM and why is it important? If you’re new to the word “SBOM” and every time you hear it think, “What bill? I don’t want to pay a bill!” then this article is for you! A “SBOM” or “Software Bill of Materials” is an inventory of the components that make up a...
Introduction to Containers on Embedded Linux
Containerized applications have been a common solution in the server and even desktop space for quite a while. More recently they've also been gaining interest on embedded projects. Containers can help decouple application development from the development of the...
Securing Build Infrastructure: Code Signing Key Protection
Recently there was a hack published for Hyundai’s Linux based infotainment head unit. The device itself had implemented security features such as signed/authenticated and encrypted images. However the encryption key was stored in the Linux build system (Yocto) setup...
Manufacturing protection: Provisioning IoT device secrets
Manufacturing Internet of Things (IoT) devices involves installing sensitive material (e.g.: keys, certificates, IP etc.) on the device. Secure provisioning of these secrets requires processor/hardware support along with special tooling or software. Using NXP i.MX8...
Linux Polkit: Implementing user space authorization on embedded platforms
Overview One of the key challenges the embedded device world faces is security. Undoubtedly, securing the embedded device is an arduous task and involves various layers, such as boot loaders, kernel, applications, and more. In this blog, we are going to look at how...
PKCS#11 with OP-TEE: Securing IoT device keys
Overview IoT devices incorporate keys / certificates for various use cases such as: authenticating to a cloud service, establishing secure network connections, securing Over-The-Air firmware update images etc. There are multiple software and hardware based solutions...
IoT security simplified with PSA Certified VigiShield
From customer expectations to cybersecurity regulations, the demand for security assurance of devices has never been greater. Yet device manufacturers find it challenging to secure Linux devices. Establishing a secure Linux platform requires deep expertise and time...
VigiShield Secure By Design for Yocto
Overview The Yocto Project is a popular choice for creating custom Linux distributions for IoT devices. When creating a custom Linux distribution one of the key challenges faced by device manufacturers is the time and expertise required to secure the distribution....
Securing U-Boot: A Guide to Mitigating Common Attack Vectors
Learn about ways in which you can protect and secure U-Boot implementations on your embedded systems. This involves signed FIT images, environment protections, and serial console disablement methods.
DM-Verity Without an Initramfs
Learn how you can implement file system verification on your embedded system without the use of an initramfs. This can significantly save boot time and storage requirements in many situations.
Yocto Security: Logging with auditd
The Linux audit framework is a security system which can provide accurate information about almost all security-relevant actions running processes may take on a system. The logs created using the audit framework can be used to investigate potential security incidents....
Yocto Security: Automating compliance using OpenSCAP
The Security Content Automation Protocol (SCAP) is a method of using certain interoperable security standards to automate evaluating policy compliance of deployed systems. In order to scan a system for compliance or vulnerabilities, there are two components involved:...
Securing your Linux Configuration (Kernel Hardening)
This article discusses the process by which your kernel’s configuration can be strengthened to protect against common security exploits. This is sometimes referred to as hardening, or specifically in this context, kernel configuration hardening.
A Linux kernel configuration is a file which defines all of the enabled (or disabled) options which are compiled in to your kernel. If you have not seen one before, they generally reside in …
Discretionary Access Control (DAC) Hardening
Discretionary Access Control hardening can further improve your embedded system’s security by limiting userspace access to proprietary intellectual property, exploitable binaries, and privileged information. The example permissions shown here are defaults produced during a demonstration Yocto build.
In Linux, a file has the following relevant parameters (when listing a file with the “ls” command):
5 Lessons Learned From the Log4j Vulnerability…and How the Embedded Industry Can Be Better Prepared for the Next One
Log4j has set the security world ablaze. With the first vulnerability (CVE-2021-44228) ranked with a CVSS score of 10 — as high as the scale goes — everyone is paying attention.
The many challenges of Linux OS / BSP security maintenance
A recent blog post by Kees Cook, a Linux security expert and Google security engineer, illustrates the challenges in maintaining the security of the Linux kernel. One of the main takeaways from the blog is: “If you’re not using the latest kernel, you don’t have the most recently added security defenses (including bug fixes).”
Going the “upstream first” route is the absolute best way of keeping the kernel secure. However, it is only part of the story.
Evaluating vulnerability tools for embedded Linux devices
Monitoring and managing vulnerabilities in embedded Linux devices presents a unique set of needs that traditional IT vulnerability tools fail to address and result in wasted efforts chasing false positives and inefficiencies due to cumbersome workflows. After evaluating multiple IT cybersecurity tools, we at Timesys ended up creating a vulnerability management tool called Vigiles, which is optimized for embedded devices. This blog aims to share the lessons learned and how the right tool can bring your security maintenance cost down while improving the security posture of the device.
Best practices for triaging Common Vulnerabilities & Exposures (CVEs) in embedded systems: Top Three Questions Answered
Keeping embedded system products secure requires ongoing, constant monitoring and management of Common Vulnerabilities and Exposures (CVEs) throughout the production lifecycle.
With the constant flood of CVEs reported each week, you need to have a process for understanding the …
Vulnerability management and triaging
With 300+ vulnerabilities being reported weekly in the US National Vulnerability Database (NVD), it is more challenging than ever to maintain the security of open source and third-party software used in embedded system products. One common approach to tackle the problem is to adopt a risk-based vulnerability management strategy in which vulnerabilities that pose the highest risk to your organization are remediated first. This blog outlines how to establish such an process as part of your software development lifecycle while keeping the maintenance cost and risk of exposure low.
Webinar with NXP: CVE triage best practices for efficient vulnerability mitigation
Securing your embedded system devices is no longer just a final step in product development.
Security today must be a continuous process, a focus at every stage of your software development, release and maintenance cycles.
That’s because today’s vulnerability environment is radically different from the past. Hundreds of vulnerabilities that may or may not affect your …
Vigiles Quick Start … because securing your products doesn’t have to be hard
There is an old saying among cybersecurity vulnerability management practitioners:
The “good guys” have to get it right every time.
The “bad guys” have to get it right only once.
That means that the “good guys” — the security professionals whose mission is to keep corporate data safe — need to monitor, analyze and respond to every vulnerability that puts their systems, users and data …
Assessing CVE exposure and mitigation effort to reduce embedded system product cybersecurity risk
Embedded system security has never been more important. Rising cyberattacks against embedded systems are increasingly putting devices and customers at risk of compromise.
This means device makers need to focus on security when products are designed and when they are managed throughout the product lifecycle.
Hundreds of new software vulnerabilities are …
BSP Lifecycle Maintenance: Top Three Questions Answered
Security is critical throughout the lifetime of an embedded system. Continually changing threat environments, new deployment modes and third-party software updates mean that the BSP software for an embedded system device can no longer remain static and “frozen.”
We explored embedded system security and best practices for maintaining a BSP throughout its lifecycle in a recent webinar with our partner NXP.
If you missed the webinar, be sure to catch the replay …
Vigiles Enhancements: Software Composition Analysis (SCA) & CVE Mitigation for Stronger Embedded System Security
A giant list of vulnerabilities does little to help you bring more secure products to market.
What matters is how you filter the list, triage the vulnerabilities, and mitigate the ones that pose the greatest risk.
That’s why the new enhancements to our Timesys Vigiles Security Monitoring & Management Service will …
Stop Chasing Vulnerability Ghosts: Why efficient vulnerability detection is essential to medical device security
To detect and correct vulnerabilities, eliminate false positives and prioritize the rest.
Every embedded system device maker should want to make security a selling point, preventing breaches or exploits, not an embarrassment if a security problem occurs. But nothing equals the liability and regulatory risk associated with medical devices.
Medical Devices: Automated Vulnerability Monitoring for Streamlined FDA Security Compliance
Reducing cybersecurity risks to medical devices is essential. Regulators like the US Food and Drug Administration (FDA) have made improving medical device security a critical focus in recent years.
This means many in the medical device manufacturing community are now rethinking how the software components of their products are secured throughout their product lifecycles.
Don’t Sweat the Threats: Join the NXP webinar on vulnerability monitoring
Security must be a top priority for devices that support critical processes.
Industrial control systems, medical devices, automotive systems and many other embedded systems must be secure. These devices need to be protected from exploits that can compromise system integrity, performance, system availability and the confidentiality of sensitive data.
That’s the focus of an upcoming webinar hosted by …
NXP Solves Vulnerability Detection Challenge for Developers with New Automated Tool
This is a summary of a blog post published in full on NXP.com.
Connecting and being connected makes us vulnerable to hackers. With the number of IoT devices forecasted to reach 20.4 billion by 2020, the need for product security becomes even more pressing.
Every week, hundreds of new vulnerabilities are …
Full lifecycle security now available for Advantech’s new product line based on NXP i.MX 8 series processors
Designing secure products is important. But the ever-changing threat landscape means that a product may become vulnerable at any time after release. That’s why we are excited to announce a new offering for stronger security across the full embedded system product lifecycle with our partner, Advantech.
Now, product developers using Advantech platforms incorporating NXP i.MX applications processors will …
New security offering with NXP: Ensure embedded system security throughout product lifecycle
We are excited to announce a new collaboration with NXP® Semiconductors that enables product developers to maintain strong embedded system security throughout their product lifecycles.
The new offering combines our Timesys Vigiles Security Monitoring and Management Service with NXP processors to streamline and simplify security management.
CVE Monitoring & Management: Timesys’ Akshay Bhat Offers Security Guidance for Embedded Open Source Systems Part 2
As discussed in last week’s posting, central to the device maintenance process and keeping devices secure after they’ve been deployed is the ongoing monitoring and managing of CVEs that affect your product components. Therefore, it’s essential to have a clear view of relevant CVEs because there are many moving parts that need to be managed.
CVE Monitoring & Management: Timesys’ Akshay Bhat Offers Security Guidance for Embedded Open Source Systems Part 1
Timesys’ Director of Engineering, Akshay Bhat, presented a session on Open Source Security at the Embedded Linux Conference North America 2019 in August. For this two-part Q&A interview, our VP of Marketing Adam Boone asked Akshay to share his views on the challenges and best practices for maintaining security in Open Source Embedded System products.
Open Source CVE Monitoring and Management: Learn the Latest at Embedded Linux Conference 2019
Every week, more than 300 new vulnerabilities affecting software systems are disclosed by security reporting services such as the Common Vulnerabilities & Exposures (CVE) database operated by the US National Institute of Standards and Technology (NIST).
If you develop embedded systems or embedded devices, keeping pace with the constant flood of new vulnerabilities, knowing which directly affect …
Vulnerability Management: Making proactive security maintenance a part of your product support processes
Too often, it seems the first notification of a software vulnerability comes from an affected customer or the publicity surrounding a high-profile data breach. Then follows the mad scramble to mitigate the vulnerability, notify customers, update products in the field and so on.
This reactive approach to vulnerability management for your embedded system products simply doesn’t fly in today’s heightened vulnerability environment.
Security Maintenance: Three essential tasks for maintaining embedded system security after release
The product development and release maintenance cycle has many predictable elements.
You know you will face time constraints for engineering to develop, test and prepare the product for production release based on the product roadmap and schedule. You’ll likewise face constraints around engineering resources, including the people and tools needed to hit the development targets.
Secure Product Management: Reducing Security Trade-offs Part 2
As discussed in last week’s posting, security often ends up taking a backseat to other considerations when you are bringing products to market or supporting ones already in production deployment.
Product managers often are faced with delivering baseline product functionality and dealing with constraints around timelines and budget. That means broader security considerations fall out of the product when these constraints force trade-offs and fundamental product requirements take priority.
Secure Product Management: Reducing Security Trade-offs Part 1
There is a decades old principle in managing any project called the “Triple Constraint” or sometimes “The Iron Triangle.”
It states that any project involves trade-offs between three constraints:
- Time: project schedule
- Cost: available resources in terms of people and budget)
- Scope: volume and comprehensiveness of …
CVE Monitoring: Knowledge of vulnerabilities and the power to secure your products
Knowledge is power.
And knowledge of vulnerabilities affecting your products gives you the power to make them more secure.
That’s why our new Vigiles vulnerability monitoring and management service incorporates the industry’s first Targeted Vulnerability & Mitigation Tracker that pinpoints vulnerabilities affecting your specific products.
Vulnerability Management: Automation ends the pain of manual DIY security
Every week, more than 300 new vulnerabilities affecting software systems are disclosed by security reporting services such as the Common Vulnerabilities & Exposures (CVE) database operated by the US National Institute of Standards and Technology (NIST).
These vulnerabilities run the gamut of low risk security concerns to critical issues. Some vulnerabilities can allow an attacker to take control of a company’s IT systems, gain access to sensitive information …
Bring more secure products to market now: Meet Timesys Vigiles™
Constant vigilance is the key to bringing truly secure products to market.
Constant vigilance is what you get with our new real-time security monitoring and management service, Timesys Vigiles.
We named the new service after the famed city watchmen of ancient Rome. Like them, Vigiles is constantly watching, scanning for threats, and …
Here comes the ‘stick’ for IoT security … or can we self-police?
Poor security of Internet of Things has led the US Federal Government to (again) consider legislation to force makers of IoT devices to improve security.
And the proposed bill comes on the heels of industry concern that IoT attacks against the US power grid are increasingly common and threaten public safety.
This week a bipartisan group of four US senators introduced the “Internet of Things (IoT) Cybersecurity ...
Embedded World Highlights: Build it faster & with stronger security
Security is becoming a critical differentiator in embedded system products across a wide range of applications.
And the tools are now available to ensure products can be more secure without sacrificing time-to-market and, in some cases, even accelerating development.
Those are key takeaways from this year’s Embedded World Exhibition and Conference that took place in Germany last week.
Is vulnerability management a regular part of your product management? (Spoiler alert: It better be.)
Effective product security starts with good product management.
And a good product manager recognizes that product security does not stop with secure design.
Effective security demands monitoring, tracking and acting on vulnerabilities on an ongoing basis …
Build it fast, and build it secure: see the latest at Embedded World
The world of embedded systems has gone through a massive transformation in recent years.
The rise of smart devices, the Internet of Things, mobile computing platforms, connected devices and a range of other innovations have driven embedded system deployments through the roof. Industry observers estimate IoT deployments alone account for 23 billion device deployments in 2018, up from 15 million in 2015. And that number is projected to triple in the next six years.
Tracking and Maintaining the Security of Embedded Systems
The deployment modes and functionality of embedded systems have evolved rapidly in recent years, thanks to widespread connectivity of Internet of Things devices and associated systems.
Yet the common security practices for most embedded systems remain largely unchanged from the days when they were isolated, air-gapped systems.
The shortfall in embedded system security is leading to sharply escalating risk of cyberbreaches. The trend …
The Risks of a ‘Stale, Abandoned’ Product
Some product management decisions are hard. Product managers are constantly weighing trade-offs among time-to-market, functionality, competitive differentiation, development costs and other factors.
But some product decisions seem like no-brainers. Would you bring an IT product to market that puts customers at significantly increased risk of security breaches, privacy violations, potentially massive fines and lawsuits?
“Of course not. That would be lunacy,” you can imagine the typical product manager as saying. Yet companies are shipping products every day that introduce this sort of …
Who is attacking IoT? What do they want?
The motivation of hackers sometimes can be plain as day. Other times, not so much.
As attacks on Internet of Things (IoT) devices and deployments escalate, it is important to understand what these attackers are trying to accomplish. Understanding these motives, after all, can help us to pinpoint why a security vulnerability represents a risk, to prioritize mitigation and defenses, and to focus responses to attacks.
This analysis is especially important if you provide products and platforms to companies deploying IoT …
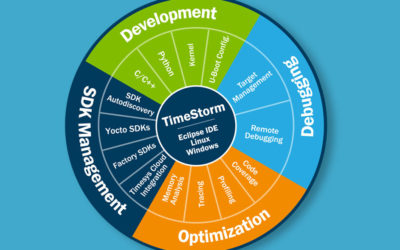
New IDE version produces shorter time-to-market for secure IoT devices and embedded Linux applications
This week we announced a new release of our TimeStorm Integrated Development Environment (IDE). TimeStorm 5.3.2 IDE is designed to streamline, simplify and accelerate the development of secure Internet of Things (IoT) and embedded Linux applications.
In an era of heightened awareness of embedded software security and device security risks, product developers need to be able to adopt security best practices without delaying the development and release …
Progress toward IoT security … a little less conversation, a little more action please
Research, reporting and commentary about Internet of Things security has made a flurry of technology headlines over the past several years. And industry observers are commenting that IoT security may finally be gaining the attention it deserves among technology decision makers.
So will 2019 be a milestone year for IoT security?
Or will more IoT security failures lead to more industry regulation, more vendor criticism and more conversation, not enough action?
‘Be Secure or Be Fined’ … 2018’s major milestones in IoT and embedded system security
As 2018 draws to a close, we’ve seen a landmark year in cybersecurity for embedded systems and the Internet of Things (IoT), marked by escalating threats, new regulation, and broader attacks.
Here’s a look back at three important IT security milestones in 2018 and a look forward with some predictions for 2019 and beyond.
2018: Year of Record Vulnerabilities
With a few days remaining in the year, the number of …
Another Record Year for Vulnerabilities … Time to Join the CIA?
This blog post is published as a guest post on Embedded Computing Design.
In mid-November, the total count of vulnerabilities reported in 2018 surpassed the total for 2017, setting a new record for vulnerabilities with six weeks left in the calendar year.
At this pace, we are on track to see the count of Common Vulnerabilities & Exposures (CVEs), the authoritative index of confirmed IT system vulnerabilities, reach 16,000 or more vulnerabilities for this year, according to …
Can products be developed quickly and be secure at the same time?
It’s perhaps the longest standing myth in IT:
You can deploy IT quickly, or you can deploy it securely. But you can’t do both.
This supposed trade-off touches virtually every aspect of IT, from product development, to market release, to customer deployment, production product maintenance, and all associated stages.
Of course, like many myths, there is a bit of truth to the trade-off. Viewed in the extreme, you could spend
What’s with the new focus on ‘Security by Design’?
As the flood of vulnerabilities continues to rise and with the new National Cybersecurity Strategy announced in the US, attention is turning to how embedded system products can be made more secure.
Almost 20 years ago, the concept of security by design was a popular new trend in software development. The focus on baking in security at product design stages was driven by the massive rise in on-line applications, e-commerce features and other Internet-connected, web-enabled software.
As these systems and applications were deployed and became widespread, the expanding attack surface made
Vulnerabilities keep piling up … time to make security a product differentiator?
Is your product the “Volvo” of embedded system products? For decades, carmaker Volvo has been known as a maker of safe vehicles.
While all makes of cars are generally much safer than in decades past, and some observers rank some other brands’ models higher in safety, there is no dispute that Volvo has made safety a cornerstone of its brand. Like other car brands have focused on qualities like luxury, reliability or the driving experience, Volvo has emphasized safety as a chief value of its products.
Another record year in vulnerabilities as the CVE storm continues
The vulnerability storm continues unabated.
The count of security vulnerabilities has reached another annual record, with six weeks remaining in the calendar year. This week the number of Common Vulnerabilities and Exposures (CVEs) hit 14,722, eclipsing last year’s total of 14,714, according to the tracking totals at CVE Details.
CVEs are being added this year at a rate of more than 300 per week on average. If that pace holds, the total should rise by another 2,000 CVEs by year’s end.
Will more embedded device makers fix security before massive fines force them to do it?
Security of smart devices is getting worse, says a penetration testing expert, who blames suppliers of connected devices that ignore security and privacy issue notifications.
Is the answer more security regulations and laws, or is it better product strategy?
Patch management for better embedded system security
Patch management remains a major headache for enterprises, according to researchers and security experts. With reported security vulnerabilities now climbing into the tens of thousands each year, busy IT departments struggle to identify and analyze the vulnerabilities that apply to their systems, and to manage all the patching needed to mitigate risks.
And the Internet of Things (IoT) poses even greater challenges for patch management.
Monitoring and managing vulnerabilities for embedded systems built with Yocto
The Yocto Project is well known for enabling product developers to quickly and easily customize Linux for Internet of Things (IoT) devices and other embedded systems. But today’s environment is marked by heightened security concerns, skyrocketing vulnerability reports, and high-profile security breaches.
Getting your embedded system product to market fast is important. But getting to market fast without a secure design and a plan for managing future vulnerabilities is a huge mistake.
Security vulnerabilities and medical devices: when the software update itself is the problem
A classic security breach vector involves exploiting weak authentication. As security researchers like to point out, failing to change default passwords for administrative access remains the top security issue for all types of IT systems.
But a related — and perhaps more devious — attack vector involves exploiting a weakness in a process that is supposed to help ensure device security in the first place: the remote system update.
Embedded system security and the IT performance tradeoff
Embedded system products are often deployed by IT managers struggling with a longstanding tradeoff: Should you sacrifice IT performance to make IT more secure?
The performance-or-security tradeoff has been the subject of technology research and industry analysis for many years. The analysis often focuses on issues like network performance or business application performance and how security measures may impede or otherwise affect throughput or access.
Security testing of embedded open source systems creates a stronger enterprise security posture
Researchers and the technology media are reporting that the average application now contains more open source software components than proprietary code. And the use of open source components in embedded systems such as Internet of Things (IoT) devices likewise is on the rise.
How is this trend affecting awareness of embedded system security and open source security best practices?
Security vulnerabilities and the Internet of Things
We’re on the verge of setting another annual record in the number of security vulnerabilities being reported. And more and more vulnerability exploits are targeting the Internet of Things.
Botnet exploits are going after IP cameras. Smart home technologies are being hacked. Even children’s toys are being hacked and used for covert surveillance. And in one bizarre case, hackers gained access to a casino’s systems through a smart thermometer in the lobby fish tank.
But these cases raise the question of what really is a vulnerability?
Vulnerability management for Internet of Things and embedded systems
The number of security vulnerabilities continues to skyrocket.
After setting a record last year, the number of reported Common Vulnerabilities and Exposures (CVEs) is on pace to set yet another record this year.
In 2017, more than 14,000 CVEs were reported, affecting a vast range of devices, systems and applications. So far in 2018, more than 12,000 CVEs have been reported, and if that pace continues, we should move past last year’s record number in the next two months.
Laying down the law on IoT security
IoT device security vaulted into the public consciousness in recent years. Media coverage of successful attacks against IoT devices and supporting systems, botnets powered by compromised devices, and a range of other security issues have raised public concern.
But now California is on the verge of enacting the first actual law in the US to mandate IoT device security.
Unfortunately, according to some in the industry, the bill now awaiting the governor’s signature will do little in its present form to improve the security of IoT, or the companies deploying it, or the people using it.
Security at IoT scale
It often helps to look at cybersecurity from the attacker’s point of view.
This approach, in fact, is the foundation of common techniques for penetration testing. That’s when “white hat” hackers will put a company’s IT systems through a range of attacks, looking for security vulnerability issues and defense gaps.
So when we consider Internet of Things device security and the defenses that protect an enterprise’s IoT deployments, it’s important to adopt the mindset of an attacker.
What’s an attacker looking for when they are prepping IoT attacks?
‘Complexity is the enemy of security’ … especially in IoT
There is an old saying in the IT security space, one that applies really across any type of security: Complexity is the enemy of security.
It’s hard to pin down exactly who coined this phrase. Among the earliest references to it are from IT security guru Bruce Schneier. And Schneier’s discussion of this principle is probably among the clearest: systems get harder to secure as they get more complex. And since our systems are getting more complex all the time, security is becoming more challenging.
Today’s poster child for the Complexity-Security inverse correlation is Internet of Things device security.
Secure boot on Snapdragon 410
Qualcomm Snapdragon processors support secure boot which ensures only authenticated software runs on the device. By configuring the processor for secure boot, unauthorized or modified code is prevented from being run. The authenticity of the image is verified by use digital signatures and certificate chain.
Secure boot process overview
On Qualcomm processors the first piece of software that runs is called Primary BootLoader (PBL) and it resides in immutable read-only-memory (ROM) of the processor. By configuring the processor for secure boot, PBL can verify the authenticity of the Secondary BootLoader (SBL) before executing it.
IoT Security: Don’t Ship Product Without It
Devices connected via IoT technology are spreading across multiple industries at unprecedented rates. But the benefits of enhanced connectivity are accompanied by increased security risks.
IoT technology is used in everything from healthcare devices, to transportation infrastructure, to industrial control systems supporting operationally critical processes.
According to Forbes, some 80 billion devices will be connected to the internet by the year 2025. In terms of customer convenience and effective performance, this trend could be game-changing for people who rely on technology to explore, work, and live.
The FBI Warns of IoT Security Issues Once Again
The US Federal Bureau of Investigation has issued a warning about Internet of Things device security issues, the latest in a continuing string of IoT attack and security vulnerability warnings from the US’s top law enforcement agency.
Attackers are using compromised IoT devices as proxies to mask various illicit activities, the FBI said, citing spamming, click-fraud, illegal trade, botnets for hire, and other crimes being committed using IoT devices.
The Bureau said IoT device vulnerabilities are being exploited by these attackers, naming routers, media streaming devices, Raspberry Pis, IP cameras, …
Why is traditional IT security failing to protect the IoT?
The traditional IT security architecture has been through a mammoth, global stress test in recent years thanks to the environment of escalating attacks and huge data breaches.
But perhaps the biggest challenge of all to the traditional IT security architecture has been in the IT evolution driven by the Internet of Things (IoT), Cloud Computing, Edge Computing and related innovations.
Data breaches in recent years have already been reaching epidemic proportions with millions of records compromised in typical breaches. Researchers report that the number of data breaches in 2017 were an order of magnitude larger than in 2005.
Make your device’s security posture stronger
If you make devices that support enterprise operational tasks, sensor data gathering, or a range of other enterprise processes, then your device’s security posture is a major concern for your customers.
But if you are not in the IT security industry, the security posture for your device may not even be something that is clearly defined in product requirements. Besides the obvious security-oriented features, such as encryption and authentication and compliance-mandated features, security requirements are often embedded in a host of other functions and processes that may be covered by your device requirements.
Maintaining strong security for your IoT device BSP
IT security has never been more of a hot button topic than it is today. Increasingly, the focus is on the security of the Internet of Things (IoT) and the embedded systems that support these devices.
And so far, the traditional enterprise security architectures and procedures are failing to protect these systems from being compromised. The evidence is trumpeted in the headlines documenting successful compromises, emerging breach patterns, and the exploding volume of vulnerability advisories.
Discovering and Fixing Vulnerabilities Quickly: Securing Embedded Open Source IoT Devices in the Wild
The web of Internet of Things (IoT) devices continues to grow each day. In fact, by the year 2020, Gartner predicts that 95% of new electronic product designs will contain IoT technology; Forbes expects at least 80 billion IoT devices to be available by 2025. But with such a vast number of devices in use across the world, how can you hope to find flaws and address vulnerability concerns in a timely manner within your own IoT products?
Open Source CVE Monitoring and Management: Cutting Through the Vulnerability Storm
14,000+ CVEs were discovered in 2017. In April of 2018 the CVE list had surpassed 100,000 entries, and that number grows every day. So how do you protect your embedded devices and open source embedded systems in IoT and IIoT deployments from this endless onslaught of security threats?
Introducing Product Protection Solutions for Devices Based on Embedded Open Source Software
Traditional IT security isn’t protecting embedded open source systems in IoT and IIoT deployments
Here at Timesys, we’ve been noticing some concerning trends when it comes to open source embedded software security and the rise of Internet of Things (ioT) and other intelligent devices. We’ve been hard at work developing a solution that can help ease your burden of carefully developing, monitoring, and maintaining security measures on your devices.
Managing vulnerabilities: Understanding patch notifications and fixing CVEs
After Notification: The Next Steps
In a previous blog, we covered how Timesys handles security monitoring and notification of open source software vulnerabilities, how to generate reports on demand for the current state of a Yocto, Buildroot or Factory build on the desktop, and how to view and generate reports on the web. If you missed it, now would be a good time to catch up before reading this post, because the next steps cover what to do …
Webinar Series: Reduce Risk with RISC – Designing and Maintaining Secure Embedded Linux Devices with Advantech RISC Platforms
The security of your device systems and software is critical for your customers. Heightened cyber-attacks, stringent privacy requirements, and increased breach risks all demand that security is baked into your product design, not slapped on as an afterthought.
Managing vulnerabilities: The importance of security notification and how to leverage Timesys’ solution
Security Is Important
No matter what industry you’re in, maintaining the security of your software is vital. It may be obvious that medical devices need to protect patients and their privacy, but a range of consumer gadgets fueling the IoT have also been targeted and used to cause real damage.
Meltdown and Spectre vulnerabilities
Google Project Zero team discovered a method to read privileged memory from user space by utilizing CPU data cache timing to leak information out of mis-speculated execution. Variants of this issue are known to affect many modern processors, including certain processors by Intel, AMD and ARM. For more details refer to this blogpost.
Trusted Software Development Using OP-TEE
This blog aims to introduce the concept of Trusted Execution Environment (TEE) and how end users can leverage open source software to safely deploy applications that require handling confidential information.
Secure Boot and Encrypted Data Storage
Secure boot ensures only authenticated software runs on the device and is achieved by verifying digital signatures of the software prior to executing that code. To achieve secure boot, processor/SoC support is required. In our experience, some of the more secure boot friendly processors with readily available documentation are NXP i.MX, Xilinx Zynq, and Atmel SAMA5 series. Some TI Sitara processors support secure boot, but might involve TI factory programming of signing keys and custom part numbers.
Securing Embedded Linux Devices
Embedded devices have unique security needs ranging from IP protection, anti-cloning / anti-counterfeit capability, device software integrity, user data protection, securing network communication, device authentication and ability to run only trusted applications. A wide range of open source technologies are available that can help implement the aforementioned security requirements. However, it is not always apparent which mechanisms are best suited for a given use case, resulting in a steep learning curve. This blog series aims at giving a high-level overview of the different methods to secure your product and help accelerate your trusted software deployment.
Software / Firmware Update Design Considerations
The Internet of Things (IoT) has quickly led to the deployment of ubiquitous, unattended devices throughout our homes, offices, factories and public spaces. In this continuously expanding connected world of devices and IoT, the need to update/upgrade your product’s software/firmware is a certainty. There is no single software update approach that fits all, but there are key questions you should consider when designing your approach. They are: Why, When, What and How.