Introduction
This is our third blog in our SBOM Generation and Vulnerability Monitoring series focusing on specific ecosystems. Today, we’ll explore the process of generating a Software Bill of Materials (SBOM) for Debian Linux-based containers and discuss the significance of Software Composition Analysis (SCA) in maintaining the security and integrity of your containerized applications.
What are SBOMs and SCA Tools?
As you may already know, SBOM stands for Software Bill of Materials and is a detailed inventory of all software components and dependencies within a project. In the context of Debian containers, maintaining an accurate SBOM is crucial due to the extensive use of deb packages and various components within the container. SCA tools help identify and manage vulnerabilities in these components, ensuring your projects remain secure.
What are Debian Containers?
Debian Containers refer to container images that use Debian as their base OS. These images are commonly used in Docker and other container platforms for deploying applications in a consistent and isolated environment.
Generating an SBOM for Debian Containers with Syft
In our testing, syft generated the most well formed SBOM. As such, Syft is our chosen tool for generating SBOMs in this series.
Steps to Generate an SBOM with Syft:
- Download and install Syft:
`curl -sSfL https://raw.githubusercontent.com/anchore/syft/main/install.sh | sh -s -- -b /usr/local/bin v1.4.1`
- Next, generate an SBOM by running this command:
`syft <source> -o cyclonedx-json=syft-debian-sbom.json`
Example for a Debian container pulled from Docker registry:
`syft debian:buster-20231120 -o cyclonedx-json=syft-debian-sbom.json`
How do You Generate a Vulnerability Report with Vigiles?
Vigiles is our SBOM management, vulnerability monitoring, and remediation tool offered. To view the above generated SBOM and generate a vulnerability report, follow these steps:
- Download the Fixup Script located here.
- Run the Fixup Script:
`python vigiles_deb_sbom_fix_up.py <generated/sbom/path> -o <optional: output/sbom/file/name>`
Example:
`python vigiles_deb_sbom_fix_up.py syft-debian-sbom.json -o debian-updated-sbom.json`
- Upload to Vigiles using the WebUI or using the vigiles-cli tool as shown below. Once uploaded, the tool will return a URL to the webUI.
`vigiles -k </path/to/key> manifest upload </path/to/sbom>`
Note: You will need an active Vigiles Enterprise subscription. If you don’t have Vigiles, you can try Vigiles Prime for free for 30-days here.
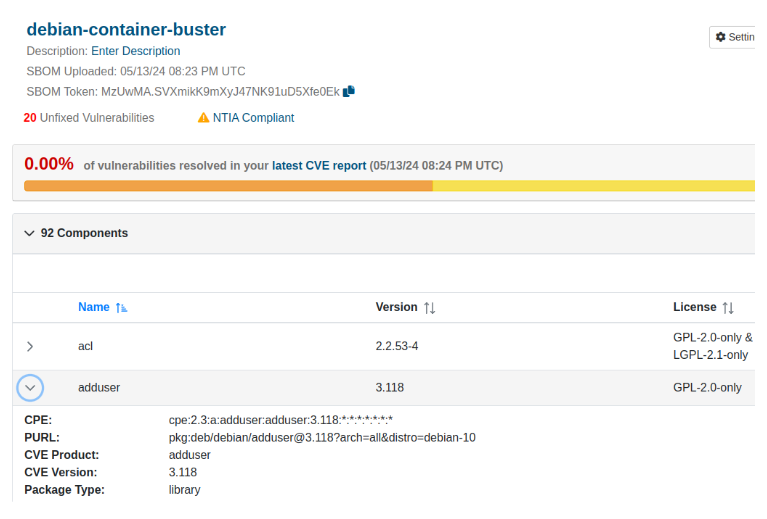
Sample SBOM WebUI View
In the Vigiles WebUI, you can view the SBOM component details such as name, version, and license information.
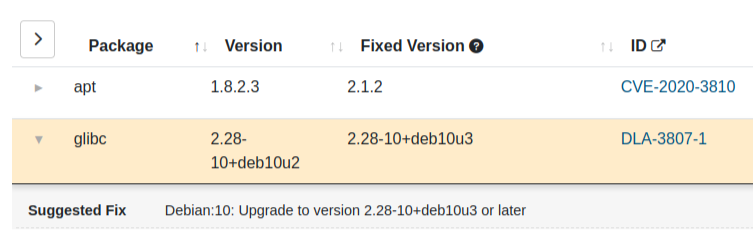
Sample Vulnerability View
In this view, you can see all the vulnerabilities associated with each package and available fixes.
Vigiles pulls from multiple security advisories, including but not limited to NVD and OSV (GitHub Security Advisory, PyPI Advisory, Go Vulnerability Database, Rust Advisory, Haskell Security Advisories, OSS-Fuzz, Debian Security Advisories, and RConsortium Advisory).
Limitations of Debian Containers
Vigiles relies on the Debian security advisory (DSA) / Debian Long Term Support Security Advisory (DLA) to report vulnerabilities and fixes for OS packages. Vulnerabilities for Debian-installed packages without a DSA or DLA will not be reported by Vigiles. These vulnerabilities are typically ones that the Debian security team has deemed as a minor issue or unimportant (in other words, won’t fix CVE’s) or the distro has reached end of its life.
At the time of writing, Syft does not contain all the elements prescribed in the NTIA minimum elements for an SBOM. Below are the missing fields in the CycloneDX JSON format:
- Dependencies
- Supplier
Other quirks:
- To avoid duplicate package entries from the SBOM, remove all previously generated SBOMs from the targeted directory before generating a new one.
Why is Vigiles the Perfect Companion to Syft?
Vigiles offers numerous benefits that make it an ideal companion to Syft:
- Curated CVE Database: Enjoy improved accuracy in CVE reporting with a meticulously curated database.
- Continuous Security Feed: Stay ahead of vulnerabilities with updates that align with your SBOMs.
- Advanced Filtering & Triage Tools: Quickly identify and prioritize vulnerabilities, streamlining the remediation process.
- Compliance Support: Easily meet industry compliance requirements for cybersecurity documentation and SBOM management.
- Integration & Collaboration: Seamlessly integrate with major Linux build systems and collaborate efficiently through tools like Jira.
Take Your Software Security in Debian Containers to the Next Level
By combining Syft’s accurate SBOM generation with Vigiles’ comprehensive vulnerability management in the Debian container ecosystem, you can significantly enhance your software’s security posture.
Vigiles not only helps in identifying vulnerabilities but also provides direct links to patches and remediation options, simplifying the process of securing your software.
Get Started with Vigiles Today
Experience the full benefits of SBOM and vulnerability management with Vigiles. Try Vigiles Prime free for 30 days and discover how it can streamline your vulnerability management process, safeguard your software, and accelerate compliance workflows. Contact us for a free evaluation of Vigiles Enterprise and take the first step towards a more secure development journey.
———————————————
Tools evaluated
- syft (version – 1.4.1); https://github.com/anchore/syft
- trivy (version – 0.49.1); https://github.com/aquasecurity/trivy
- cyclonedx-linux-generator (version – latest); https://github.com/CycloneDX/cyclonedx-linux-generator
- distro2sbom (version – 0.4.0); https://pypi.org/project/distro2sbom/
